- March 13, 2020
- Posted by: Alex Chen
- Category: How-To

Background
Part of Azure production support work includes identifying certificates that are about to expire in Azure App services and
App Registrations (and their associated Client Secrets and Certificates). You can manually check these things, and that works great. However, if you are supporting dozens, or even hundreds, of app services and certs, then the manual approach quickly becomes a pain for both determining when certificates will expire and if new certificates were successfully deployed.
This script provides a more efficient way.
Download this script and save it with the .ps1 extension .
Usage
Analyze the expiration status of the certificates installed in each Resource Group and location, only the latest version (later Expiration Date) will be shown if multiple versions are detected in single Resource Group and location. Please note that even through the certificates are installed inside an Azure App Service, they are shared by all App Services in the same Resource Group and location.
.\Analyze-AppServiceCerts.ps1
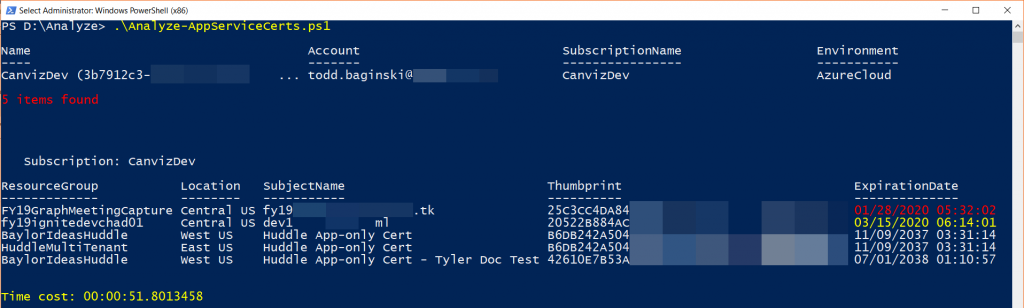
Search the Resource Groups and locations which have the specified cert installed, only the latest version (last Expiration Date) will be shown if multiple versions are detected in single Resource Group and location.
.\Analyze-AppServiceCerts.ps1 -k ‘[PLACEHOLDER_OF_THUMBPRINT]’
.\Analyze-AppServiceCerts.ps1 -k ‘contoso.com’
Enumerate all unique certificates installed in App Services, only the latest version (last Expiration Date) will be shown if multiple versions are detected in single Resource Group and location.
.\Analyze-AppServiceCerts.ps1 -ul
Scan all App Registrations (and associated Client Secrets and Certificates ) and certificates referenced in the App Service configurations, also accepts additional keywords to scan specific App Services only.
.\Analyze-AppServiceCerts.ps1 -cfg
.\Analyze-AppServiceCerts.ps1 -cfg -k ‘[WEBAPP_NAME_KEYWORDS]’
Limitations
- .NET Core config files are not supported yet.
- First party apps are not supported.
- The config name of the app registrations must contains a ‘ClientId’ or ‘Audience’ (e.g. ida:ClientId), if there’s any new patterns that come out later, the script will need to be updated accordingly.
- A large desktop resolution (e.g. 1920 * 1080) is required to see all report columns properly in a large table.